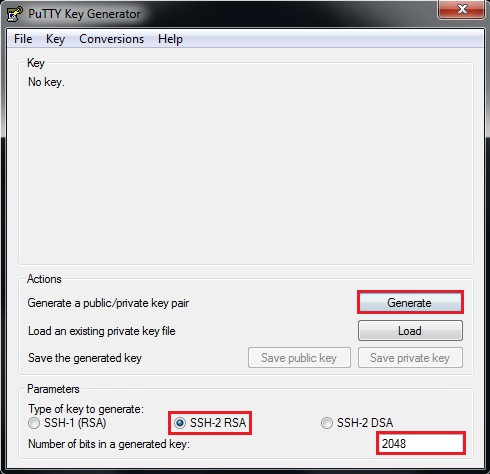
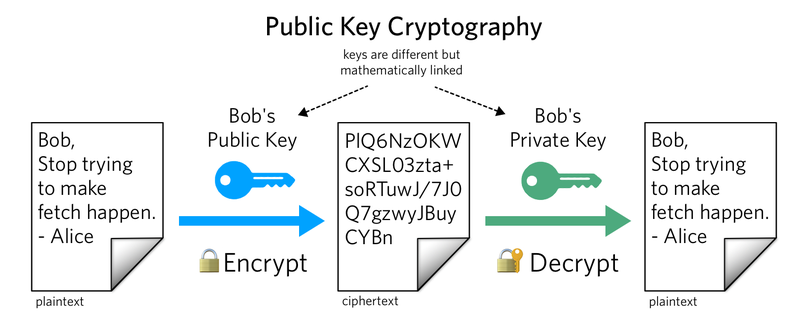
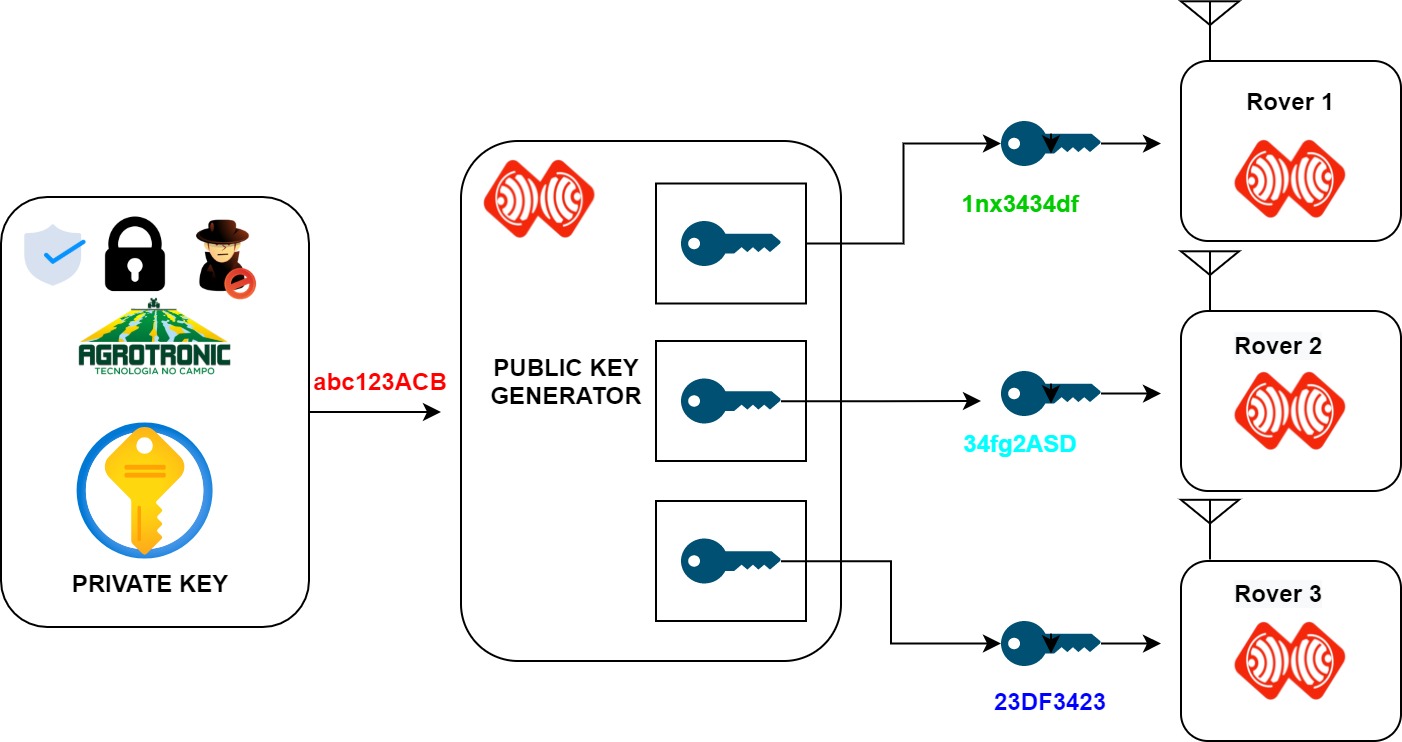
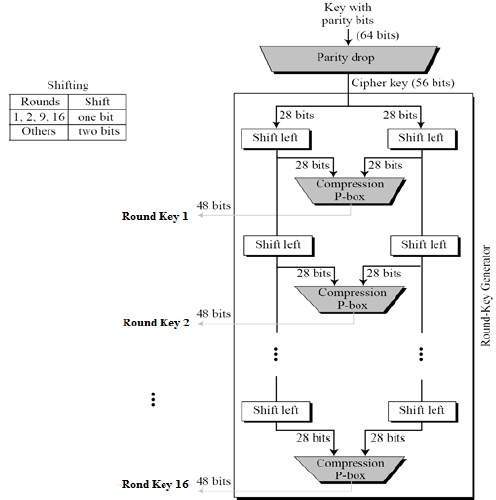
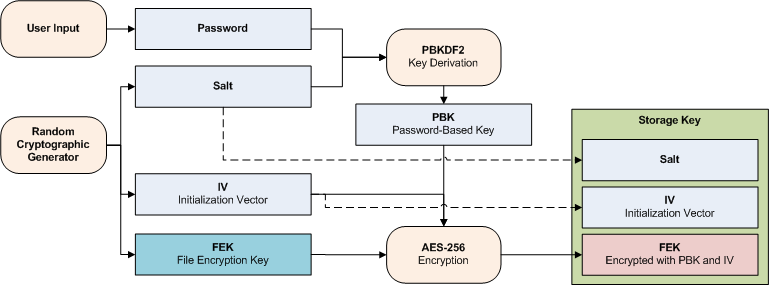
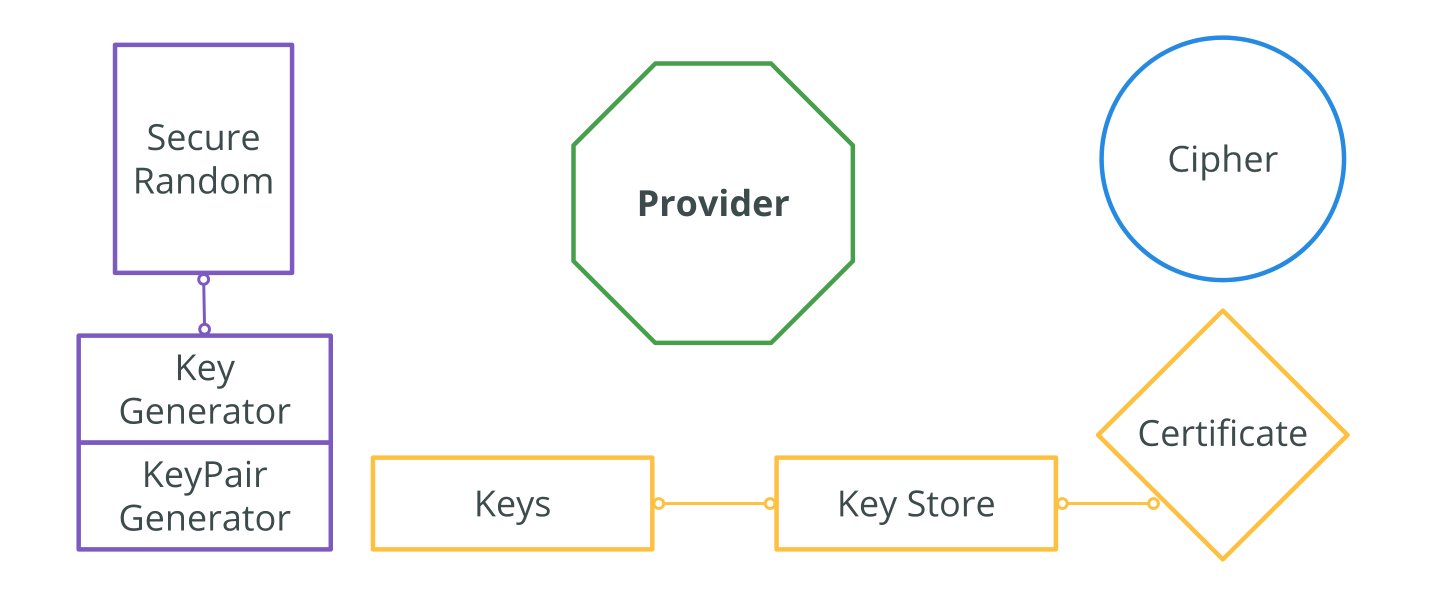
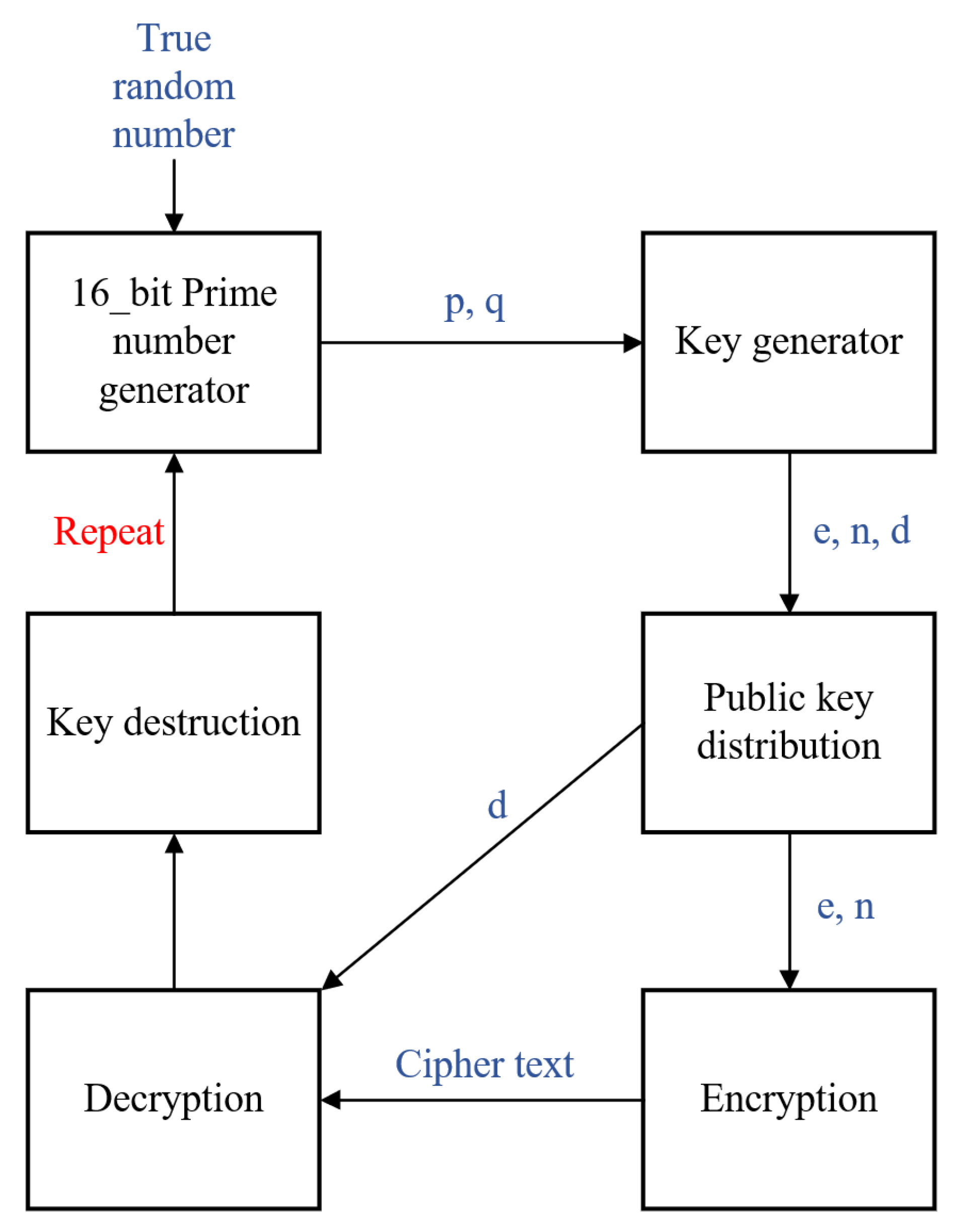
Enhanced key-generation algorithm using MRMCTT in Data encryption standard algorithm | Semantic Scholar

Generation of Cryptographic Keys from Personal Biometrics: An Illustration Based on Fingerprints | IntechOpen
File:KG-83 Key Generator Encryption-Decryption Equipment - National Cryptologic Museum - DSC08014.JPG - Wikimedia Commons

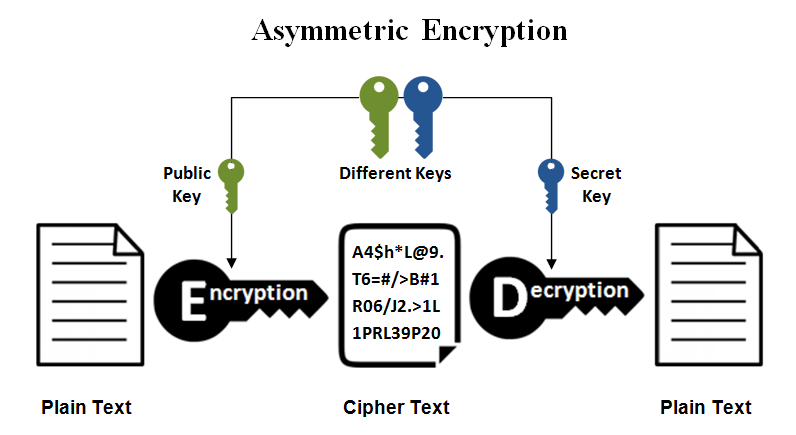
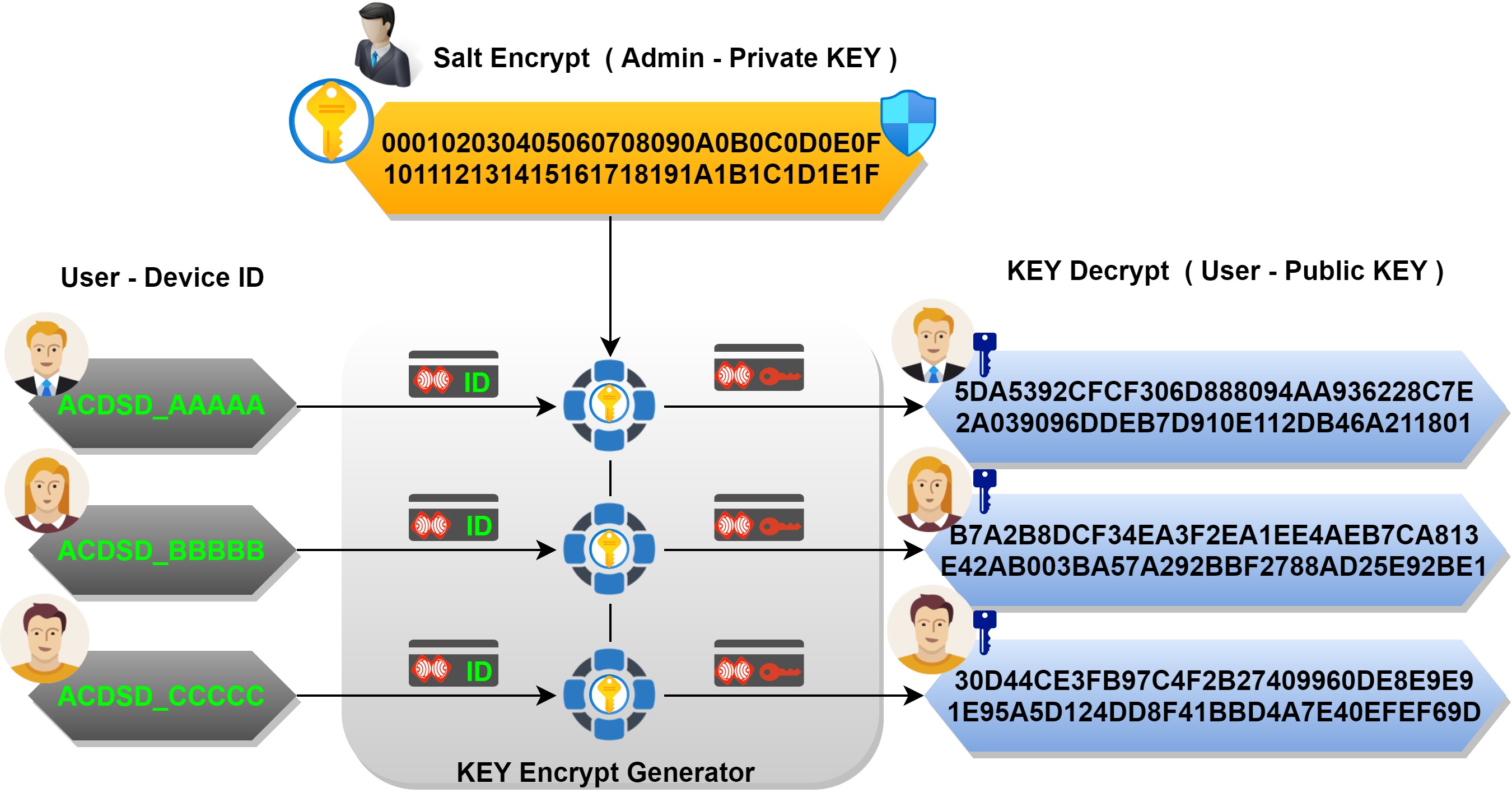

![MS-DRMND]: Content Encryption for AES in Counter Mode | Microsoft Learn MS-DRMND]: Content Encryption for AES in Counter Mode | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-drmnd/ms-drmnd_files/image007.png)