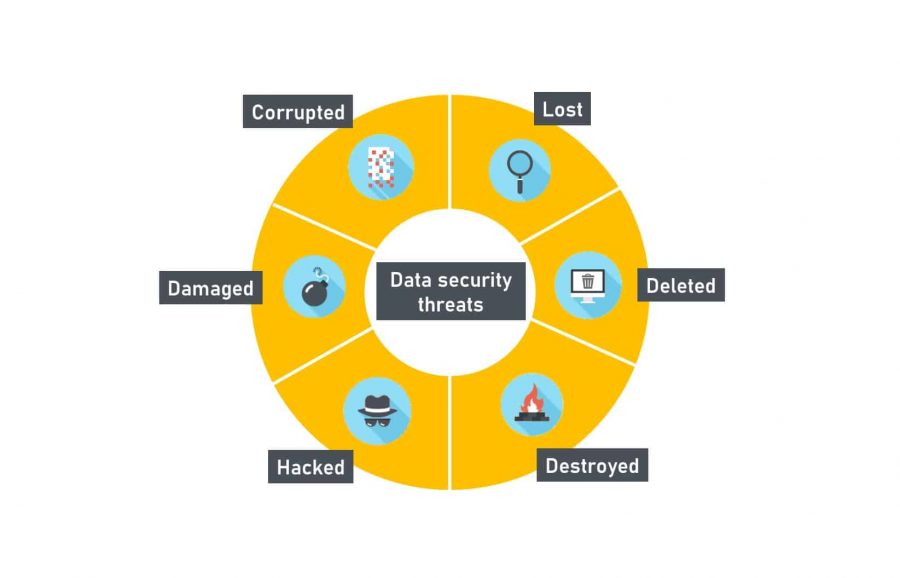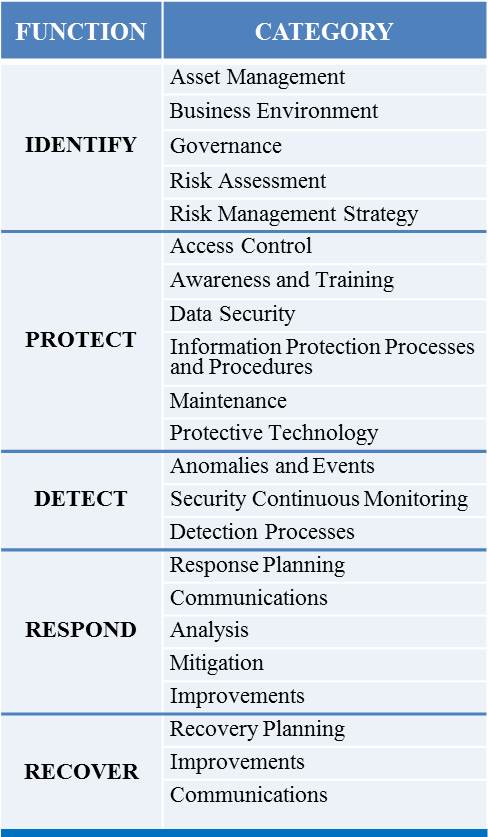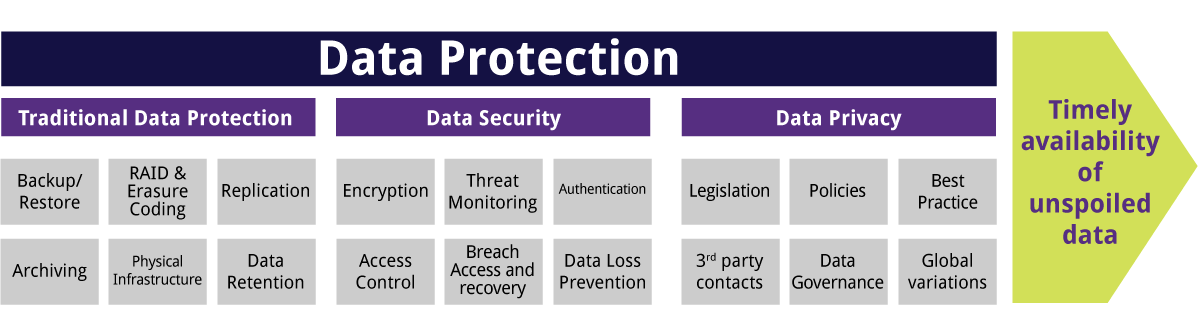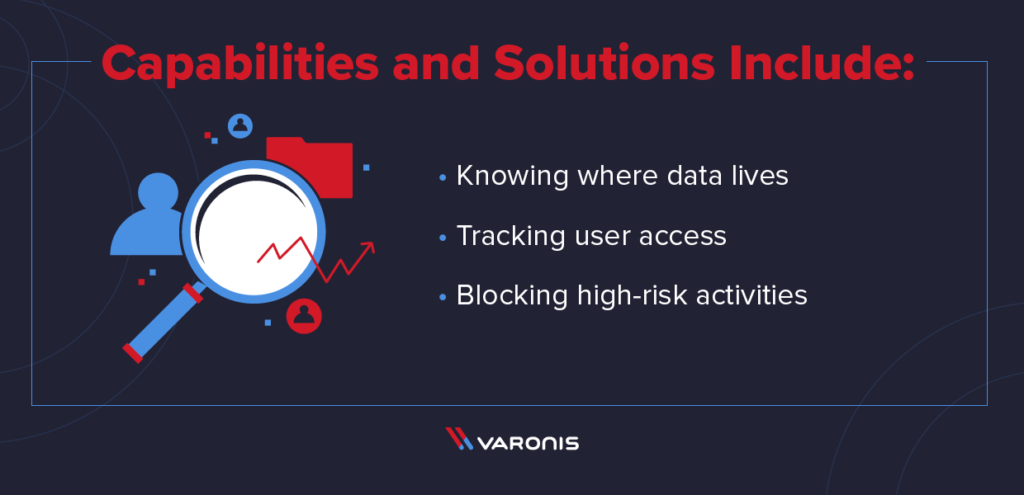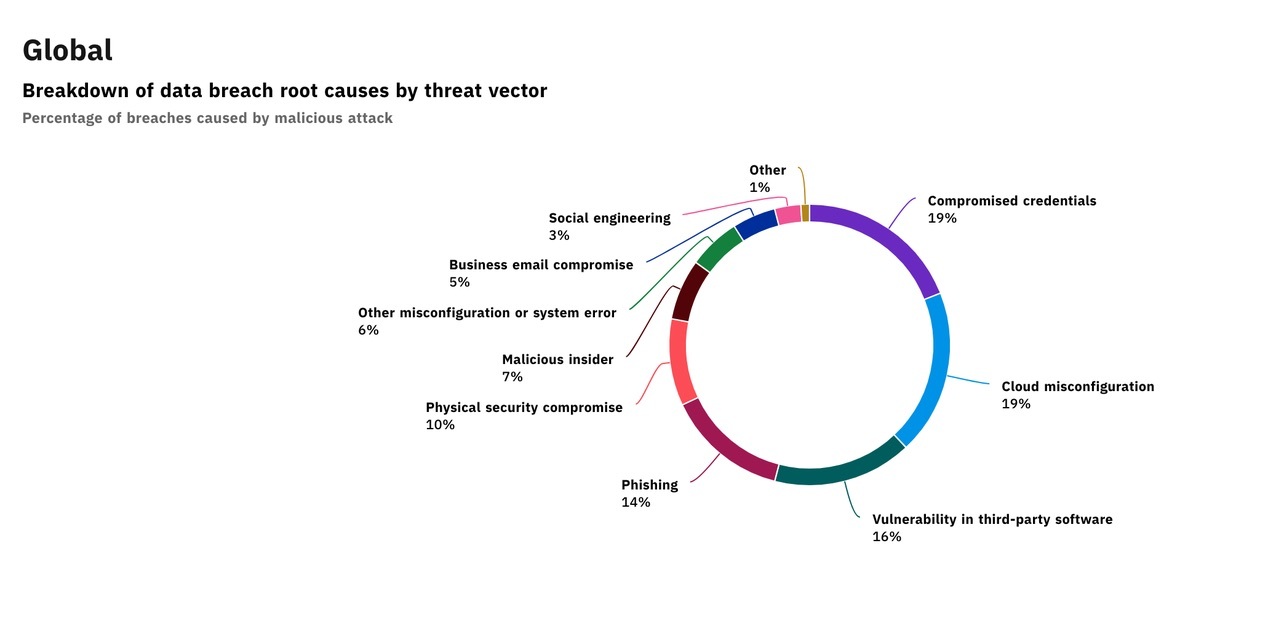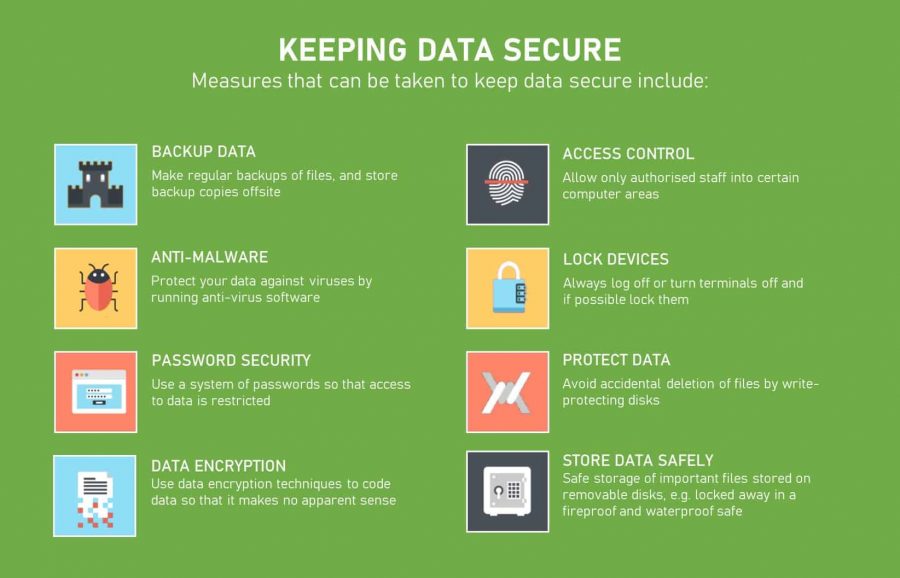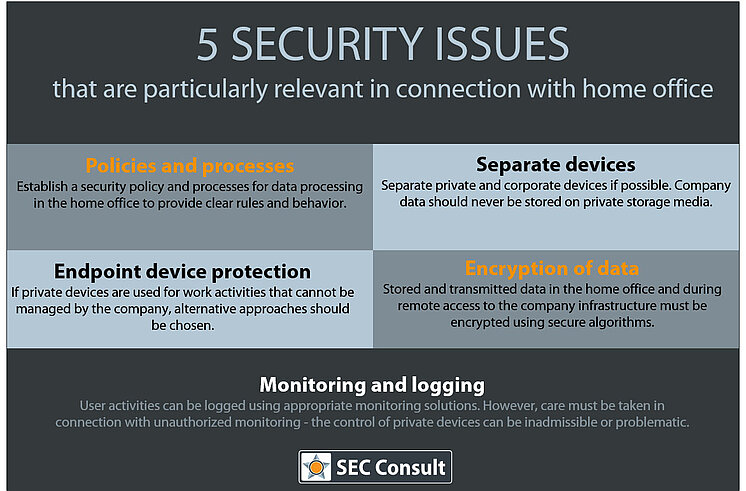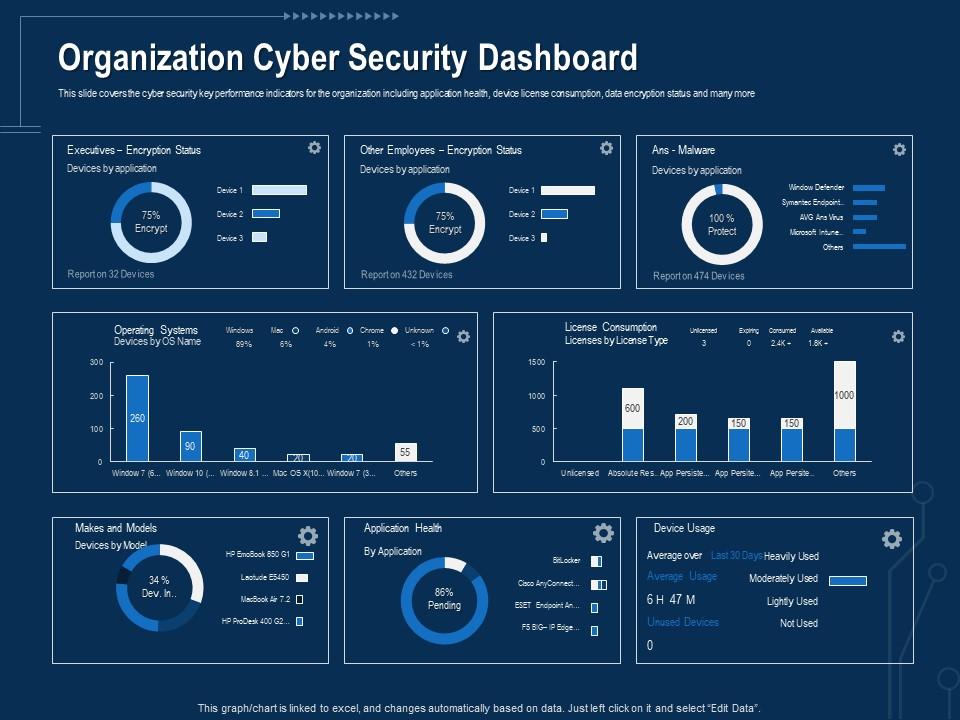
Corporate Data Security Awareness Organization Cyber Security Dashboard Ppt Powerpoint Guidelines | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

mHealth Data Security, Privacy, and Confidentiality Guidelines: Companion Checklist — MEASURE Evaluation

9 Important Elements to Corporate Data Security Policies that Protect Data Privacy | 2016-05-10 | Security Magazine




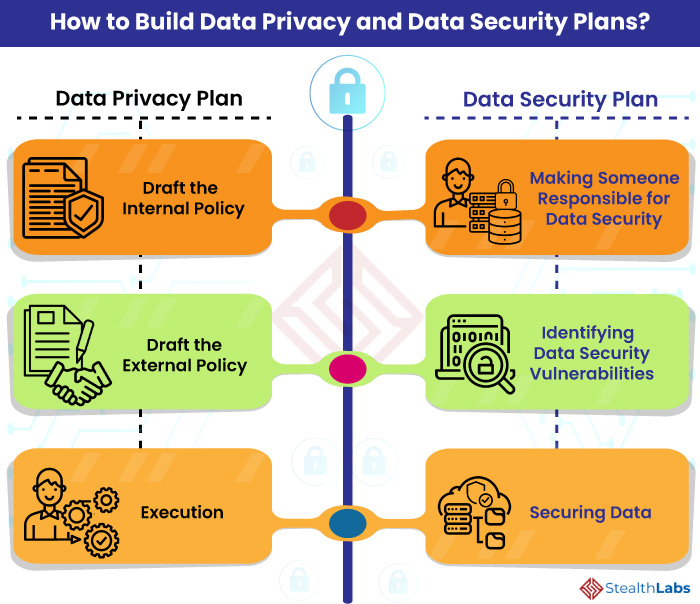
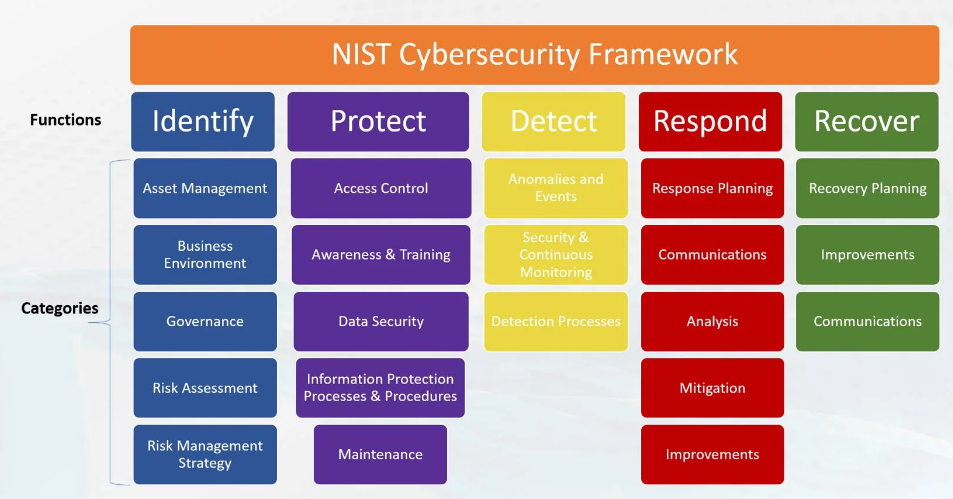

![22 Best Practices for Protecting Data Privacy in 2022 [Infographic] - TitanFile 22 Best Practices for Protecting Data Privacy in 2022 [Infographic] - TitanFile](https://www.titanfile.com/wp-content/uploads/2022/03/Protecting-Data-Privacy-in-2022-Infographic-2.png)