A Multi Agent Framework to Detect in Progress False Data Injection Attacks for Smart Grid | SpringerLink
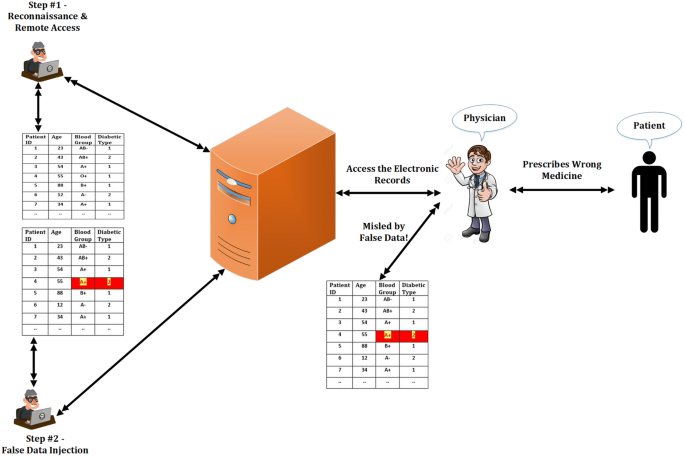
False data injection attack (FDIA): an overview and new metrics for fair evaluation of its countermeasure | Complex Adaptive Systems Modeling | Full Text

Impact of optimal false data injection attacks on local energy trading in a residential microgrid - ScienceDirect
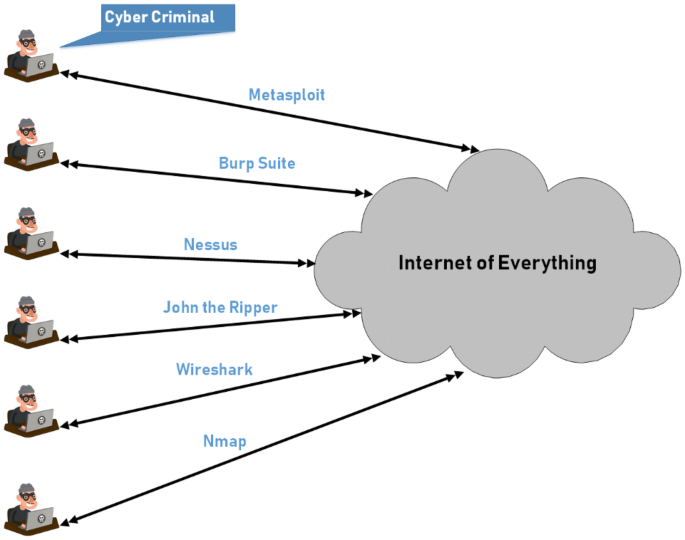
False data injection attack (FDIA): an overview and new metrics for fair evaluation of its countermeasure | Complex Adaptive Systems Modeling | Full Text